A single crypto investor has lost a staggering $2.6 million in stablecoins after falling victim to two phishing attacks within just three hours. The sophisticated scam employed a method known as a zero-value transfer—an emerging onchain phishing tactic that is raising alarms across the crypto community.
Phishing Strikes Twice in Three Hours
The incident, reported on 26 May by crypto compliance firm Cyvers, involved two separate transactions. First, the victim mistakenly sent $843,000 worth of USD Tether (USDT), followed by another $1.75 million a few hours later. Both transfers were directed to addresses controlled by scammers, who used clever onchain methods to trick the user.
The scam is a glaring example of how fast and effective phishing attacks in decentralised finance (DeFi) have become. It also highlights a troubling evolution in crypto scams, where even experienced users can fall prey to fraudulent tactics embedded in blockchain transactions.
How Zero-Value Transfers Work
Zero-value transfers exploit the “From” function in token smart contracts. In this case, the attacker sends a zero-token transaction from the victim’s wallet to an address they control. Because the transaction involves zero tokens, it does not require the victim’s private key signature, making it easy for scammers to plant these transactions into the blockchain.
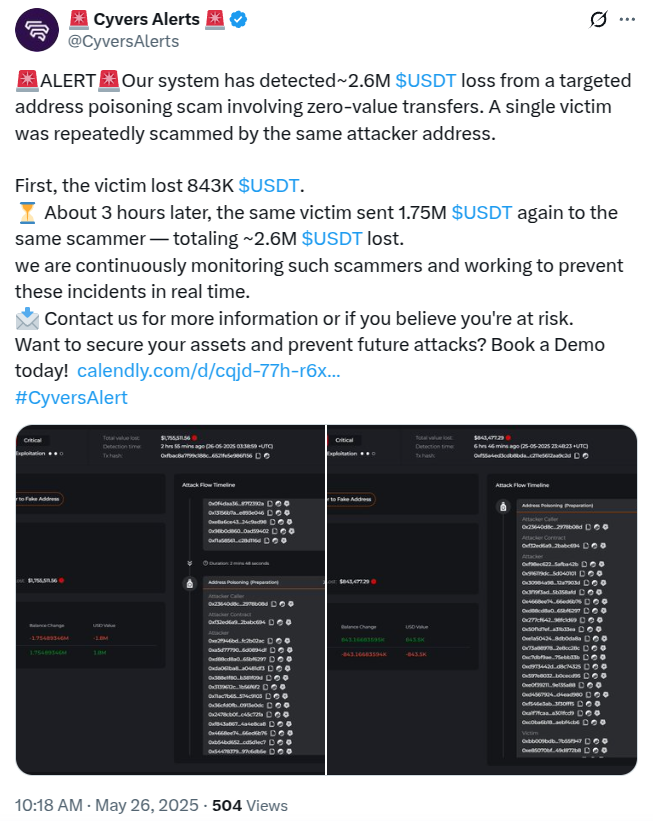
Later, when users check their transaction history, they may see this spoofed address listed and mistakenly assume it’s a legitimate or previously used recipient. Trusting this address, they may send actual funds—resulting in major losses.
This tactic is particularly dangerous because it creates a false sense of security, as the addresses appear in verified transaction logs. It combines social engineering with technical manipulation to exploit a user’s trust in their transaction history.
Evolution of Address Poisoning
Zero-value transfers are considered a more advanced iteration of an older scam known as address poisoning. In that method, scammers send tiny amounts of crypto from addresses that closely mimic the victim’s own address—often with identical starting and ending characters. The intention is to confuse the user into copying the wrong address from their transaction history or clipboard.
This newer approach, however, bypasses the need for even minimal transfers and embeds a seemingly legitimate address into the user’s history, creating an even more convincing trap.
Attackers also craft addresses with similar alphanumeric patterns, exploiting users’ habit of verifying only the beginning and end of wallet addresses before sending funds.
Wider Threat Across Blockchain Networks
A recent study from January 2025 revealed the alarming scale of these types of attacks. Between July 2022 and June 2024, over 270 million poisoning attempts were recorded on major blockchains like BNB Chain and Ethereum. Of these, around 6,000 attacks succeeded, resulting in over $83 million in stolen funds.
The sheer volume of attempted attacks underscores the growing sophistication of crypto fraudsters and the need for improved onchain threat detection tools.
Tech Solutions and Industry Response
In response to the rise of address poisoning scams, cybersecurity firm Trugard and onchain trust platform Webacy announced a new artificial intelligence-based detection system in early 2025. According to initial reports, the tool has demonstrated a 97% success rate in identifying poisoning attempts across previously documented cases.
While promising, experts stress that technology alone cannot eliminate the threat. Users must also exercise caution and verify wallet addresses thoroughly—preferably using full address matching rather than relying on clipboard history or partial characters.
Lessons from a Costly Mistake
This case serves as a stark reminder of the risks involved in crypto transactions, especially in decentralised environments where there are no banks or intermediaries to reverse mistakes.
Cyvers and other compliance firms are urging platforms to integrate address verification prompts and automated fraud detection to help users avoid falling for similar scams. However, until such features become widespread, individual vigilance remains the best defence.
As blockchain technology grows more complex and widespread, so too do the methods employed by malicious actors. For now, the burden of safety continues to rest heavily on the shoulders of individual crypto holders.

Leave a Reply