In a troubling but revealing shift, hackers in 2025 have increasingly turned away from exploiting code vulnerabilities and are instead targeting crypto users directly. According to the latest report from Web3 cybersecurity firm CertiK, over $2.1 billion has been stolen this year through crypto attacks, the majority of which stem from social engineering schemes rather than smart contract flaws.
A Dangerous Shift: Code to Human Behaviour
CertiK’s co-founder Ronghui Gu noted a major change in hacker strategy: instead of targeting weaknesses in smart contracts or blockchain protocols, attackers are now focusing on human error and psychological manipulation.

Appearing on Cointelegraph’s Chain Reaction X Spaces show on 2 June, Gu explained:
“Smart contracts or blockchain code itself was the weakest point, but now the attackers feel like the weakest points may come from human behavior rather than the code.”
Social engineering schemes such as phishing, wallet address poisoning, and private key mismanagement have become the most effective tools in a hacker’s arsenal. These tactics don’t require high-level technical skills; instead, they prey on user naivety, carelessness, and operational lapses.
Wallet Compromises Dominate 2025 Losses
The majority of this year’s crypto thefts, well over half are attributed to wallet compromises. Phishing attacks alone cost the industry over $1 billion, with 296 separate incidents recorded in 2024, according to CertiK’s Hack3d report.
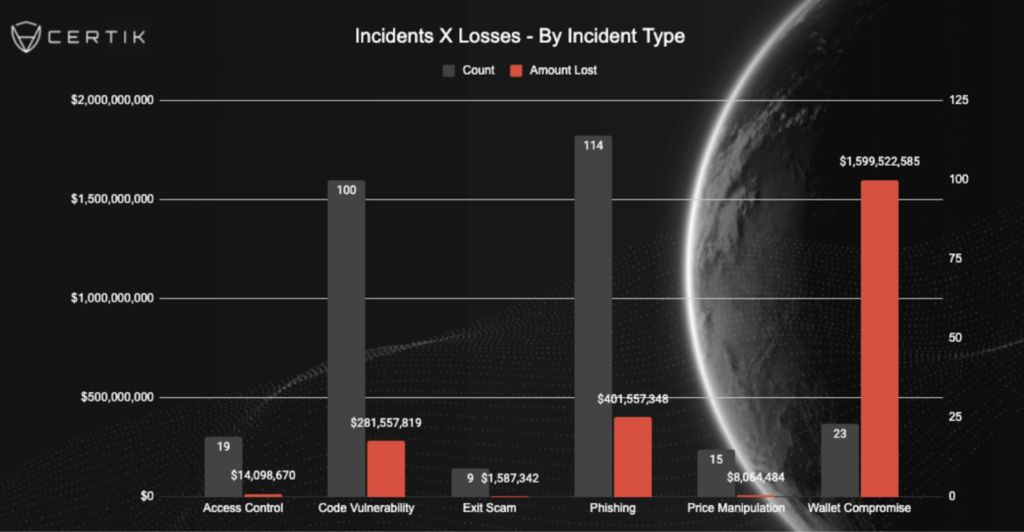
These scams usually involve fraudulent links that trick users into revealing private keys or seed phrases. In some cases, malicious actors manipulate users into sending funds to fake addresses that closely resemble legitimate ones, a method known as address poisoning.
A shocking example came in April 2025, when $330.7 million in Bitcoin was stolen from an elderly American citizen through a carefully orchestrated social engineering scheme. This single incident demonstrates the scale and precision of these attacks, which no longer rely on technological exploits but instead on manipulating people.
Lazarus Group Behind Record-Breaking Hack
The largest crypto exploit in history took place on 21 February 2025, when the notorious Lazarus Group, a North Korea-linked cybercrime syndicate, compromised the security of Bybit exchange, making off with a staggering $1.4 billion.
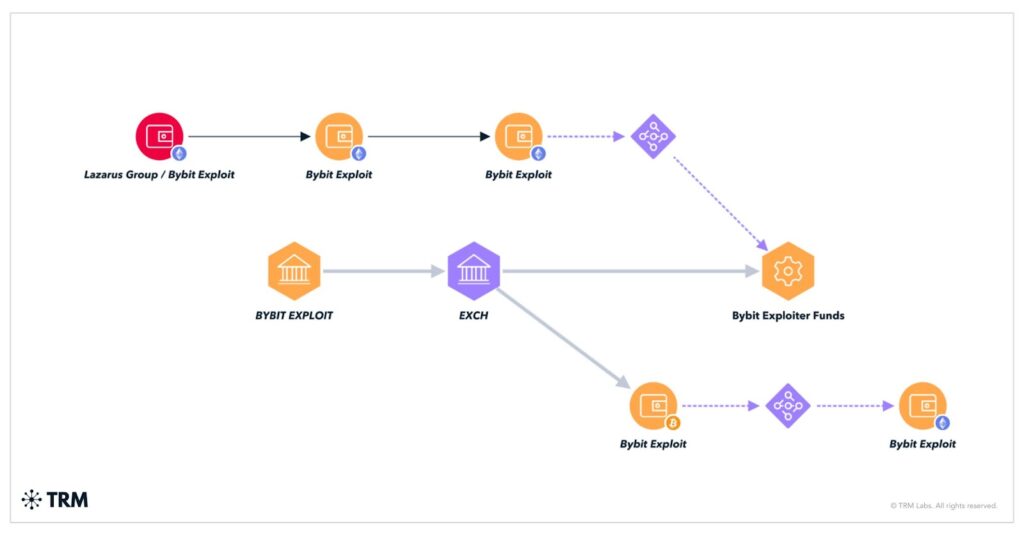
This single breach accounted for over 60% of the total losses in 2025, underscoring how high-value targets remain a focus for sophisticated threat actors. The Lazarus Group’s success was not rooted in blockchain code manipulation, but rather in human-centred attack vectors, again proving that people, not protocols, are the new weakest link.
Industry’s Path Forward: Focus on Users
With code becoming increasingly secure, experts are urging the industry to pivot its security priorities. Gu emphasised the importance of proactive measures, including:
- Better wallet security solutions
- Advanced access controls
- Real-time transaction monitoring
- Simulation tools to identify suspicious activity before it’s executed
As attackers evolve, so too must the strategies used to protect against them. Education, user interface design, and ecosystem-wide initiatives to improve operational hygiene are now just as crucial as any technical audit or protocol upgrade.
Final Thoughts
The rise in social engineering attacks signals a critical turning point for crypto security. With $2.1 billion stolen so far in 2025, largely due to human error, the sector must act swiftly to bolster user defences. As Gu aptly noted, “Attackers always target the weakest point.” Today, that point is no longer smart contract code, it’s the user.

Leave a Reply