Crypto exchange BigONE has confirmed a major security breach resulting in the loss of around $27 million worth of digital assets. The attack, discovered on July 16, targeted the exchange’s hot wallet infrastructure, a system used for storing cryptocurrencies that are actively in use for transactions.
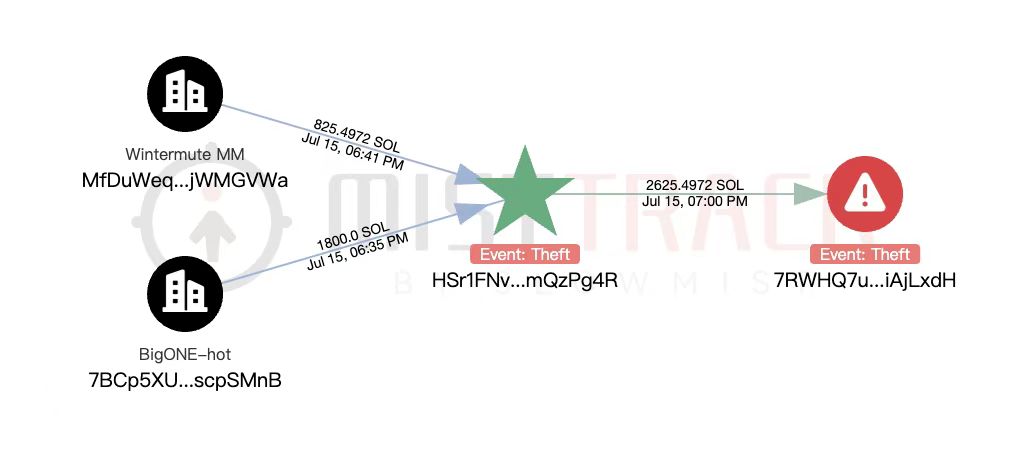
According to BigONE, its real-time monitoring system flagged unusual activity, which triggered an internal investigation. It was soon revealed that the breach stemmed from a third-party intrusion, not a flaw in BigONE’s internal private key management. The affected tokens include 120 Bitcoin (BTC), 350 Ether (ETH), millions of USDt (Tether), and other tokens such as CELR, SHIB, and SNT, across several blockchain networks including Bitcoin, Solana, and Tron.
BigONE assured users that all private keys remain secure, the attack vector has been identified and contained, and the threat has been neutralised.
Security Flaws and Attack Method
Blockchain security firm Cyvers investigated the breach and concluded that the attacker gained access via a compromised CI/CD pipeline or server management channel. These systems are crucial for deploying software updates and managing server environments. Once inside, the attacker modified BigONE’s business logic, bypassed key risk-control checks, and began executing unauthorised withdrawals.
The hack began with the deployment of malicious binaries on account-operation servers. The attacker initially withdrew 350 ETH, valued at around $1.1 million, before scaling up the operation to include other major crypto assets. All stolen funds were later consolidated into a single wallet address, likely for laundering and obfuscation purposes.
Cyvers pointed out several critical vulnerabilities in BigONE’s systems:
- Single-point failure in hot wallet management
- Lack of pre-transaction validation
- Insufficient code integrity controls
- Poor network segmentation between the build environment and wallet servers
The attacker also converted some stolen assets into WETH (Wrapped Ether), routing them through intermediary wallets to prepare for laundering via decentralised exchanges or mixing services.
BigONE Pledges to Cover All Losses
In response to the breach, BigONE announced it will fully reimburse affected users. The company has already activated its internal security reserve fund, which includes assets like BTC, ETH, USDt, Solana, and Mixin (XIN), to cover the damage.
“For other affected mainstream and non-mainstream tokens, we are actively securing external liquidity through borrowing mechanisms to restore the platform wallet as soon as possible,” BigONE stated.
The exchange is now working closely with blockchain security firm SlowMist to trace the attacker’s wallet and monitor the flow of stolen funds.
Call for Stronger Exchange Security
The BigONE hack is another reminder of the growing risks facing centralised and decentralised platforms alike. Yehor Rudytsia, an on-chain security researcher at Hacken, said the attack underscores the importance of securing CI/CD pipelines, controlling third-party dependencies, and implementing continuous monitoring across both on-chain and off-chain systems.
Rudytsia also emphasised the importance of automated incident response tools, which can help exchanges halt ongoing attacks and potentially recover funds before they are laundered.
Just a day before the BigONE breach, another platform Arcadia Finance, a DeFi protocol on the Base blockchain was exploited for $3.5 million, showing that the crypto industry remains a high-value target for cybercriminals.
The $27 million hack on BigONE adds to the growing list of high-profile crypto security incidents in 2025. Although the exchange has pledged to reimburse its users, the attack exposes critical infrastructure flaws that must be addressed. It also reignites discussions about hot wallet security, DevOps hygiene, and the importance of rigorous incident response systems for all crypto platforms. As the digital asset market matures, ensuring the security of user funds must remain a top priority.

Leave a Reply