A massive supply chain attack has shaken the crypto industry, with hackers infiltrating widely used JavaScript packages to steal digital assets during transactions. Security experts describe the incident as the largest attack of its kind, given the scale and reach across the global developer ecosystem.
How the Hackers Struck
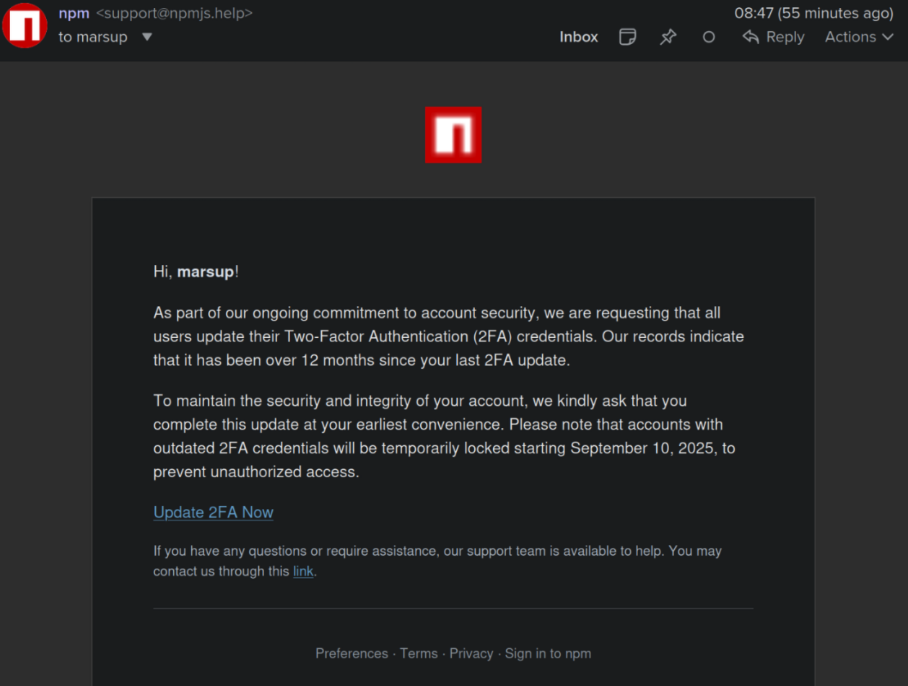
The attack was first reported by BleepingComputer, which revealed that hackers gained access to NPM package maintainer accounts through sophisticated phishing campaigns. Fraudulent emails, designed to appear from “support@npmjs.help,” urged maintainers to update their two-factor authentication credentials.
When maintainers clicked the malicious link, their accounts were compromised, enabling attackers to inject malware into trusted JavaScript libraries. In total, 18 packages were affected, collectively downloaded more than 2.6 billion times each week.
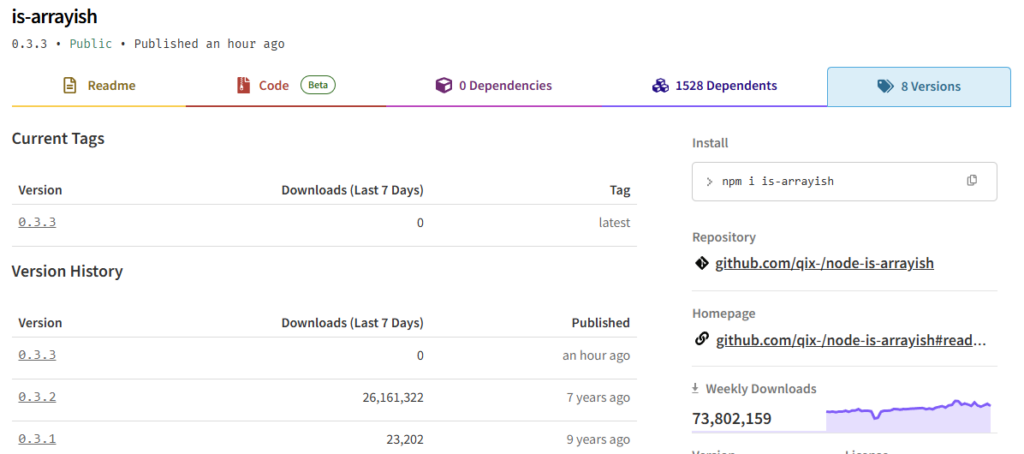
Some of the most popular libraries, including chalk (300 million weekly downloads), debug (358 million) and ansi-styles (371 million), were compromised. Given their ubiquity in web development, the breach effectively put the entire JavaScript ecosystem and by extension, a huge number of crypto applications at risk.
A Direct Threat to Crypto Transactions
Unlike typical malware that targets personal devices, this attack embedded malicious code into tools developers use to build applications. The injected code functions as a browser-based interceptor, monitoring network traffic for crypto transactions across Ethereum, Bitcoin, Solana, Tron, Litecoin and Bitcoin Cash.
When a user initiates a transfer, the malware silently replaces the intended wallet address with one controlled by the attackers, just before the transaction is signed.
Aikido Security researcher Charlie Eriksen highlighted the sophistication of the exploit:
“What makes it dangerous is that it operates at multiple layers: altering content shown on websites, tampering with API calls and manipulating what users’ apps believe they are signing.”
This makes it exceptionally difficult for end users or developers to detect fraudulent behaviour.
Expert Warnings and Immediate Risks
Ledger CTO Charles Guillemet cautioned crypto users about the severity of the ongoing threat. With billions of downloads across compromised libraries, the possibility of malicious code infiltrating countless crypto-related applications is very real.

While hardware wallet users remain largely protected as they can physically verify addresses and amounts before signing, software wallet users face heightened risks. Guillemet advised strongly against making on-chain transactions without a hardware wallet for now:
“If you don’t use a hardware wallet, refrain from making any on-chain transactions for now.”
He added that while it remains unclear whether attackers can directly extract seed phrases, the scale of the compromise makes this scenario impossible to rule out.
Scale and Sophistication of the Attack
The incident is being described as the most widespread supply chain attack in history due to both the scope of infiltration and its precision targeting of crypto. By compromising trusted libraries downloaded billions of times weekly, attackers gained unprecedented access to applications and wallets at the development level.
Researchers traced the stolen credentials back to “websocket-api2.publicvm.com,” indicating a coordinated and well-prepared operation. This is not the first such attack in 2025: in July, eslint-config-prettier (30 million weekly downloads) was compromised, while March saw a wave of malware injected into 10 widely used NPM libraries.
Looking Ahead
This incident underscores a pressing vulnerability in the software supply chain: developers and end users alike are only as safe as the code they rely on. For crypto users, the stakes are especially high, as attackers can directly siphon funds without leaving visible traces.
With the scale of compromised packages, researchers expect ripple effects across the crypto ecosystem for months. Until patches and secure versions are confirmed, experts stress caution, particularly for those not using hardware wallets.
The attack highlights the urgent need for stronger package security, developer vigilance and end-user protections. For now, the advice is clear: verify before you trust and use hardware wallets whenever possible.

Leave a Reply