Binance founder Changpeng Zhao (CZ) has claimed he was recently targeted by state-sponsored hackers, possibly from the North Korean Lazarus Group, in an apparent attempt to steal his account credentials.
Taking to social platform X (formerly Twitter), CZ revealed he had received a notification from Google warning him that attackers “may be trying to steal your password.” The alert specifically suggested that the attempted breach could be part of a state-backed cyber campaign.
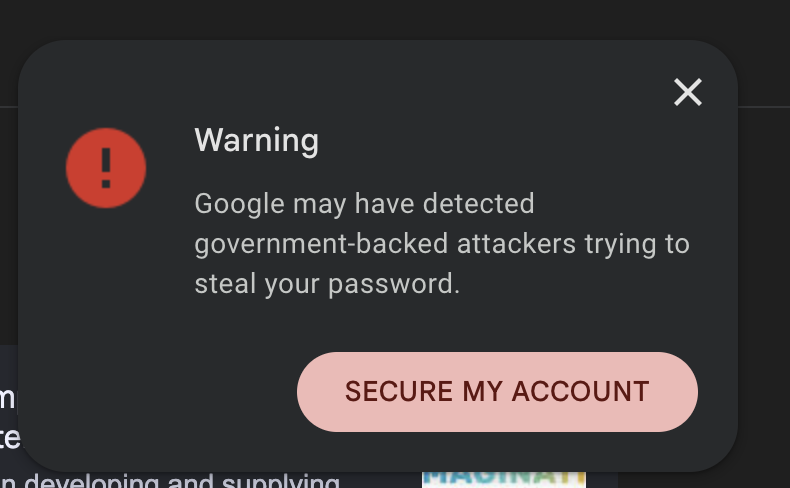
“I get this warning from Google once in a while. Does anyone know what this is? North Korea Lazarus? Not that I have anything important on my account. But stay SAFU,” CZ wrote, referring to his popular crypto safety slogan, “Stay SAFU.”
The Binance founder assured his followers that the targeted account did not contain sensitive information but urged the community to remain cautious, adding that such attacks are becoming increasingly common across the crypto ecosystem.
Community Responds with Security Advice
Following CZ’s post, several crypto users and cybersecurity enthusiasts weighed in. One user, Crypto Jargo, noted that Google’s state-sponsored warning is relatively rare and usually triggered for journalists, researchers, or individuals associated with sensitive industries.
The user further explained that while these alerts do not always mean an immediate hack attempt, they serve as a serious precautionary signal. Jargo also advised CZ and others receiving similar warnings to:
- Change their passwords immediately,
- Use two-factor authentication (2FA) via an authenticator app instead of SMS, and
- Review connected devices for any suspicious logins.
CZ’s post quickly gained traction across the crypto community, with many expressing concern about the growing frequency of phishing and impersonation attempts aimed at high-profile figures in the digital asset space.
Lazarus Group: North Korea’s Cybercrime Arm
The Lazarus Group, widely believed to be sponsored by the North Korean regime, has long been associated with large-scale cryptocurrency heists and cyber espionage.
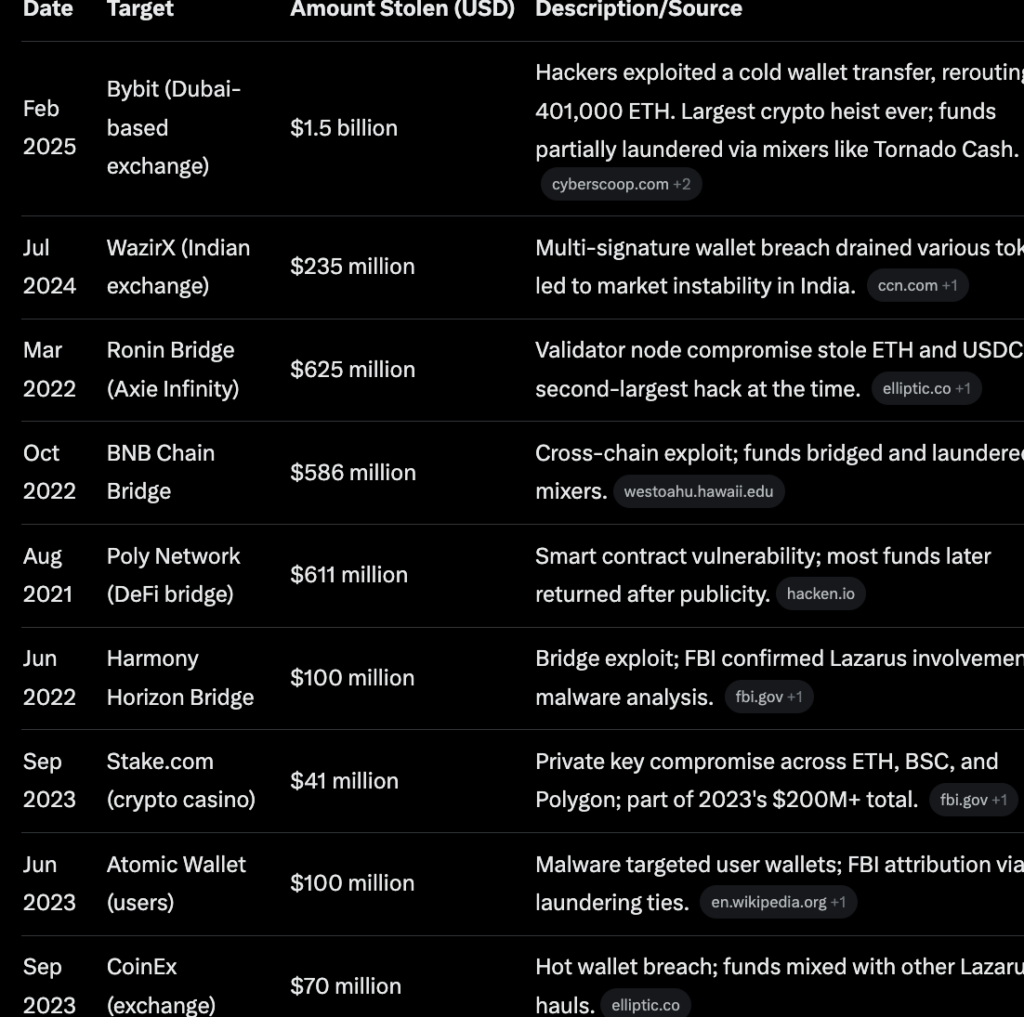
Since 2017, the group has reportedly stolen more than $6 billion in crypto assets from exchanges, DeFi protocols and individuals. Their operations have evolved to include sophisticated phishing, malware distribution and AI-powered deepfake recruitment scams.
In 2025 alone, Lazarus-linked hacks have set new records. The year has already witnessed over $2 billion in crypto thefts, nearly triple the previous record of $1.35 billion set in 2022. This includes the $1.5 billion Bybit breach in February, the largest crypto heist in history, allegedly attributed to the same North Korean outfit.
Beyond direct hacks, the group has increasingly turned toward social engineering attacks targeting executives, developers and key stakeholders within the crypto industry.
Growing Threat to Crypto Leaders and Platforms
CZ’s experience underscores a worrying trend in the digital asset sector, a shift from protocol-level exploits to personalised attacks on crypto leaders and influencers.
Cybersecurity researchers have observed a rise in fake job offers, deepfake video scams, and phishing emails designed to compromise individual accounts and wallets. These attacks aim to exploit trust and human error rather than technical vulnerabilities.
Binance and other major exchanges have repeatedly warned their users about such evolving tactics. CZ himself has publicly addressed several incidents involving AI-generated impersonations of his likeness used to lure unsuspecting investors.
While CZ downplayed the seriousness of the latest warning, the incident reflects the growing sophistication of state-linked cyber operations seeking to infiltrate the crypto ecosystem.
A Call for Vigilance in the Crypto Community
As the crypto industry continues to expand and attract institutional interest, state-sponsored hacking groups see digital assets as lucrative targets for financial gain and political leverage.
CZ’s public disclosure serves as both a warning and a rallying call for the community to remain alert. Strengthening security through strong passwords, non-SMS-based authentication and device hygiene remains essential.
With 2025 shaping up to be the most active year for crypto cybercrime on record, the line between personal and institutional risk is blurring fast. As CZ put it, even if there’s “nothing important” on your account, staying SAFU has never been more important.
Leave a Reply