Coinbase has suffered a $300,000 loss in token fees after mistakenly approving assets to a 0x Project smart contract. The error allowed a maximal extractable value (MEV) bot to drain the funds from the exchange’s corporate wallet. While no customer funds were affected, the incident has been described by security experts as an “expensive lesson” for the platform.
How the Mistake Happened
According to security researcher Deebeez from Venn Network, Coinbase’s corporate wallet interacted with the 0x “swapper” contract on Wednesday. The swapper is a permissionless tool designed to facilitate token swaps, not to receive token approvals.
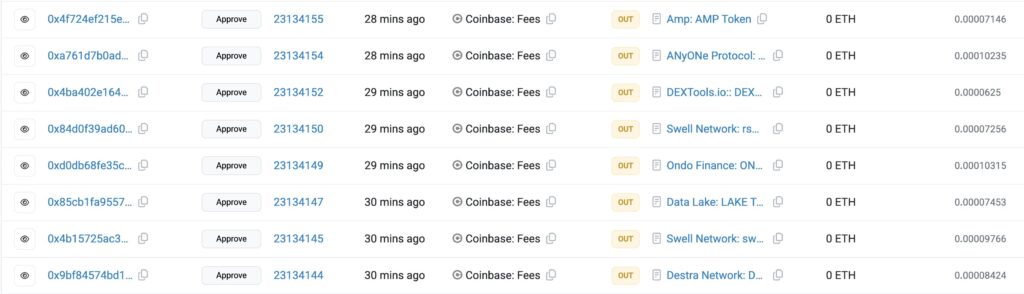
Because it is open for anyone to call and perform arbitrary actions, granting token approvals to such a contract leaves assets vulnerable to immediate theft. Once Coinbase approved several tokens to the contract, the MEV bot was able to exploit the permissions and move the tokens out instantly.
The MEV Bot Waiting for Its Moment
The MEV bot involved in the incident had reportedly been “lurking in the dark,” waiting for users to make such an error. This particular swapper contract has previously been linked to issues with Zora claims on the Base network, where similar token approvals exposed funds to theft without exploiting any code vulnerabilities.
Shortly after Coinbase approved tokens including Amp, MyOneProtocol, DEXTools, and Swell Network, the MEV bot acted. It called the swapper contract and transferred all approved tokens from Coinbase’s fee receiver account into its own addresses.
Deebeez commented that for the bot, “their dream came true thanks to Coinbase,” underscoring how opportunistic MEV strategies can be when dealing with misconfigured permissions.
Coinbase’s Response and Damage Control
Philip Martin, Coinbase’s Chief Security Officer, confirmed the incident and attributed it to a configuration change in one of the company’s corporate DEX wallets. He stressed that the issue was isolated and did not affect customer funds.
Following the theft, Coinbase revoked all token allowances granted to the swapper contract and moved remaining corporate wallet funds to a new address to prevent further risk.
The platform has not disclosed whether it plans to attempt recovery of the lost funds, though in most MEV bot-related incidents, recovery is rare unless the attacker voluntarily returns the assets.
MEV Bot Exploits: A Recurring Crypto Risk
This is not the first time MEV bots have been at the centre of high-value crypto incidents.
- April 2024: A MEV bot lost $180,000 in Ether after an attacker exploited a flaw in its access control. The attacker swapped the ETH for a worthless token through a malicious pool created in the same transaction.
- 2023: A rogue blockchain validator exploited MEV bots engaged in “sandwich trades,” stealing $25 million worth of WBTC, USDC, USDt, DAI and WETH.
These cases highlight how MEV (Maximal Extractable Value) activity, where bots exploit blockchain transaction ordering, remains a double-edged sword. While MEV bots aim to profit from market inefficiencies, they themselves can become victims when security or configuration lapses occur.
A Costly Lesson in Permission Management
The Coinbase incident is a reminder that token approvals in decentralised finance carry significant risk, especially when interacting with permissionless contracts. Without strict controls and monitoring, even large, well-funded exchanges can fall victim to opportunistic exploits.
For now, Coinbase’s loss may be relatively small compared to past industry hacks, but it serves as a warning: in the fast-moving DeFi world, one wrong approval can be all it takes to drain a wallet.

Leave a Reply